A mobile app targeting both iOS and Android users primarily from China, Korea, and Japan was first identified by Lookout Threat Intelligence team in December 2020. The apps conduct spyware activities by offering escort services while they steal personal information from the victim’s device. The goal of the attackers behind this data exfiltration of personal information is extortion or blackmail.
This particular type of scam is commonly called “Sextortion” and it typically targets multiple countries. These applications are often disguised as messaging, camera, and utility apps and are designed to exfiltrate data such as:
- Contacts
- SMS data
- Location information
- Images from device storage
Technical Analysis
During our routine threat hunting exercise, Cyble Research Labs came across a Twitter post that mentioned spyware masquerading as a Korean video app named “동영상“.
Researchers at Cyble downloaded the malware samples and performed a detailed analysis, based on which, we determined that the malware is a variant of spyware and uploads the victim data to a Command & Control (C2) server.
APK Metadata Information
- App Name: 동영상
- Package Name: org.nnnmbook.sytyd
- SHA256 Hash: 0bda73046fd733164877071d11318ec6dd56a6ea4e773c70ed5a3c8f7a244478
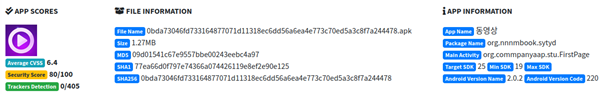
Figure 1 represents the metadata information of the application.
The malware has a set of permissions, out of which the attackers leverage three permissions to collect contacts, SMSs, and the victim’s location. These dangerous permissions are listed in Table 1.
| Permissions | Description |
| INTERNET | Allows applications to open network sockets |
| READ_PHONE_STATE | Read-only access to phone state |
| READ_CONTACTS | Access to phone contacts |
Table 1 Permission used for malicious activity
Upon simulating the app, they observed that it initially requests users for permission to read contacts. Once the app has this permission, it loads the app’s main activity, as shown in Figure 2.

The app uses the permissions granted by the users to perform these activities on the users’ devices:
- The app reads the contacts from the compromised device and stores them in the array list

- Collected contacts are stored in a JSON file and are uploaded to a C2 link as shown in figure below.

- The application also has a code function to read and collect SMS data from the compromised device.

- As shown in Figure 6, the collected SMS details are stored in a JSON file and are uploaded to the C2 link as represented below.

- Upon finding the functions being called, where the collected contacts and messages are sent via C2 link, the app further connects to the function that performs additional activities such as collecting albums and device details.

The app synchronizes the user’s device data with the C2 login page used by the attacker to fetch the stored sensitive information.

Conclusion
Despite having been around for a long time, spyware still poses a significant threat as the Threat Actors responsible are constantly adapting and using various encryption techniques to avoid detection. This makes the removal of spyware nearly impossible. Thus, users should exercise caution while installing applications.
SAFETY RECOMMENDATIONS:
- Keep your anti-virus software updated to detect and remove malicious software. Verify the publisher before installing the app. Go to the actual companies website for the app you want, and confirm the apps information and details before installing.
- Uninstall the application if you find this malware on your device.
- Keep your system and applications updated to the latest versions.
- Use strong passwords and enable two-factor authentication.
- Download and install software only from trusted sites and official app stores.
- Verify the privileges and permissions requested by apps before granting them access.
MITRE ATT&CK® Techniques- for Mobile
| Tactic | Technique ID | Technique Name |
| Defense Evasion | T1406 | Obfuscated Files or Information |
| Credential Access/Collection | T1412 | Capture SMS Messages |
| Discovery | T1421 | System Network Connections Discovery |
| Discovery | T1426 | System Information Discovery |
| Collection | T1432 | Access Contact List |
| Collection | T1507 | Network Information Discovery |
| Impact | T1447 | Delete Device Data |
Indicators of Compromise (IoCs):
| Indicators | Indicator type | Description |
| 0bda73046fd733164877071d11318ec6dd56a6ea4e773c70ed5a3c8f7a244478 | SHA 256 File Hash | Analysed Malicious file |
| hxxp://206.119.173[.]23:8080/m/uploadSms.htm | URL | C2 Link |
| hxxp://206.119.173[.]23:8080/m/sychonizeUser.htm | URL | C2 Link |
| hxxp://206.119.173[.]23:8080/m/openVip.htm | URL | C2 Link |
| hxxp://206.119.173[.]23:8080/m/login.htm | URL | C2 Link |
| hxxp://206.119.173[.]23:8080/m/uploadAlbum.htm | URL | C2 Link |